Light Bell: A Smart Doorbell System for Individuals with Hearing Impairments
Detailed Research and Creative Development Process :
The “Light Bell” project began with identifying a significant challenge faced by individuals with hearing impairments: the inability to hear traditional doorbells, which can lead to missed visitors or deliveries and even safety concerns. The idea was to create a system that would alert these individuals using visual cues instead of auditory ones.
To develop this concept, I conducted extensive research into existing products and technologies, such as visual doorbells and smart-home systems. I analyzed their strengths and weaknesses, noting that many lacked customization options and integration with modern smart-home ecosystems. This research phase also involved studying how Bluetooth and Wi-Fi technology could be leveraged to connect the doorbell system to various devices within the home.
I then moved on to the ideation phase, where I explored different ways to create a user-friendly and effective visual alert system. This involved sketching out various designs, experimenting with materials, and considering the overall form and function of the device. My sketches included ideas for how the system would look, the types of lights to be used, and how the mobile app interface would function. I also considered the practical aspects of installation and how users could easily customize their alerts based on their preferences.
Throughout this process, I consistently sought feedback from peers and potential users. I shared my initial ideas and sketches with classmates and individuals who are hard of hearing, which provided valuable insights into what features would be most beneficial. This feedback led to several iterations of the design, where I refined the system to be more responsive to user needs, such as adding a camera feature for visual confirmation of visitors and offering a wider range of color options for the alerts.
The final design was a culmination of these efforts, resulting in a prototype that is both functional and aesthetically pleasing. The process from start to finish was a clear path of research, ideation, feedback, and refinement, ensuring that the final product met the needs of its intended users.
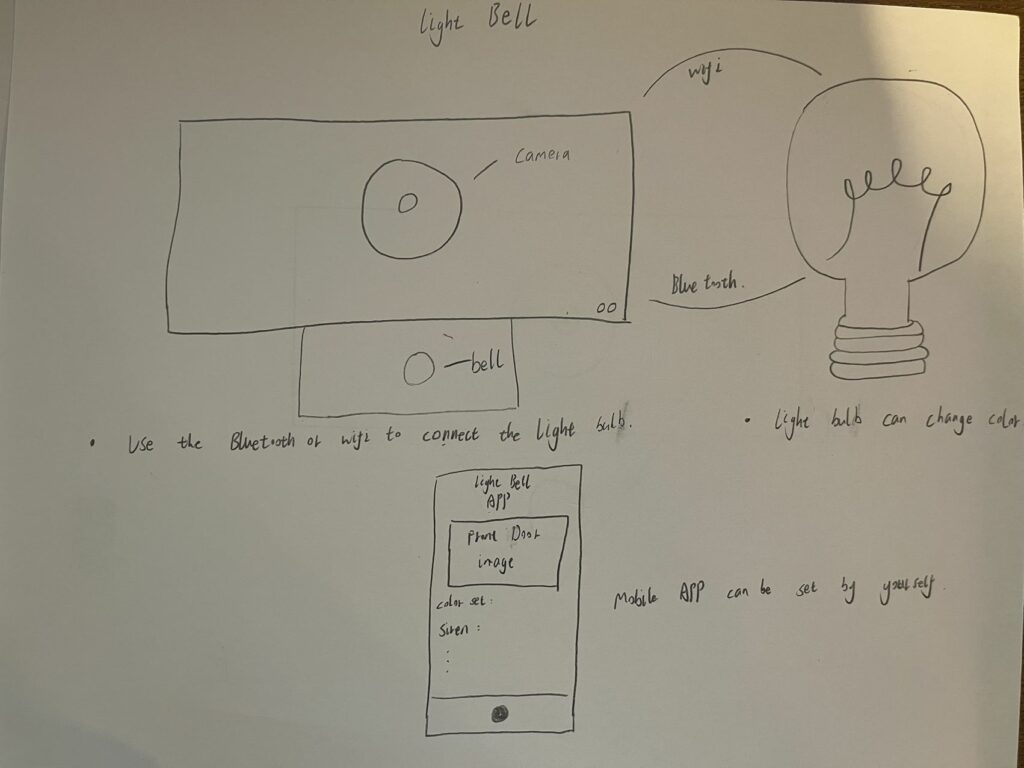
Problem:
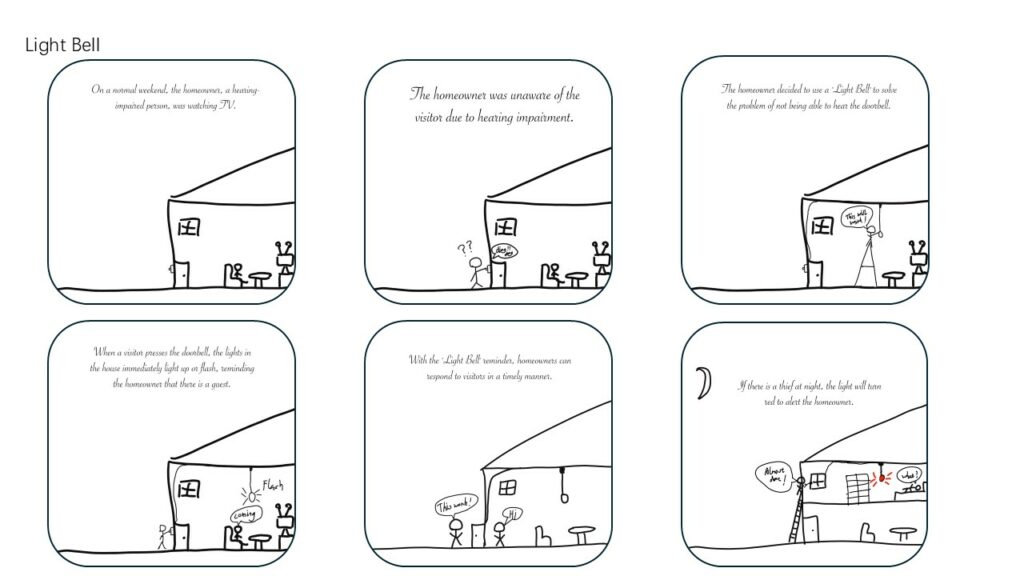
Many people with hearing impairments face challenges in knowing when someone is at their door. Traditional doorbells rely on sound, which is ineffective for those who cannot hear. As a result, they might miss important visitors or deliveries, leading to frustration and potential safety concerns. The need for a solution that effectively alerts individuals with hearing impairments to someone at their door is crucial, especially in environments where they are alone or in larger homes where they might not be near the entrance.
Solution:
The solution to this problem is a product called Light Bell, a doorbell system specifically designed for people with hearing impairments. The Light Bell is a modern, inclusive adaptation of the traditional doorbell. When a visitor presses the doorbell, instead of producing sound, the system triggers lights inside the home to flash, immediately alerting the homeowner of the presence of a visitor.
However, Light Bell doesn’t stop at just flashing lights. It is designed with a variety of customizable features to accommodate different needs. The lights can be set to different colors or flash patterns based on user preferences or the type of visitor (e.g., blue for familiar faces, red for potential unknown visitors). Additionally, the system is smart-home compatible, allowing integration with mobile devices, so users can receive alerts on their phones or smartwatches, giving them flexibility and peace of mind, even when they are not near the lights.
Evidence of Trying New Methods to Solve Problems and Develop Creative Ideas:
The development of the Light Bell involved several innovative approaches to problem-solving. One of the main challenges was ensuring that the light system would be effective in different lighting conditions and for different types of users. To address this, I experimented with various types of light bulbs and flash patterns, ultimately settling on LED bulbs that could change color and intensity based on user preferences. This approach allowed for maximum customization and ensured that the alerts would be noticeable even in bright daylight.
Another challenge was integrating the system with existing smart-home technology. I explored different ways to connect the doorbell system to other devices, such as using Bluetooth and Wi-Fi, to ensure seamless integration. This involved researching the best practices for smart-home connectivity and testing different configurations to find the most reliable and user-friendly setup.
I also explored the user experience in-depth, considering how individuals with hearing impairments would interact with the system. A mobile app that allows users to customize their alerts, view real-time video from the front door (if the device includes a camera), and receive notifications on their phones or smartwatches. This was a new approach for me, as it required learning about app development and user interface design, but it was crucial in creating a system that was both accessible and easy to use.
Asking Meaningful Questions to Develop Innovative Solutions:
Throughout the project, I posed several key questions that guided the development of the Light Bell. For instance, I asked, “How can I ensure that the visual alerts are effective in all lighting conditions?” and “What features would make this system more useful and convenient for individuals with hearing impairments?” These questions prompted me to think critically about the design and functionality of the product, leading to the development of features such as customizable light settings and smart-home integration.
I also considered the broader impact of the product, asking, “How can the Light Bell improve the overall quality of life for its users?” and “What other challenges do individuals with hearing impairments face that this product could help address?” These questions encouraged me to think beyond just the immediate problem of missing visitors and consider how the product could be part of a larger system that enhances home safety and accessibility.
Written Work Includes Evidence of Depth of Understanding and Articulation of Ideas:
In this project, I demonstrated a deep understanding of the challenges faced by individuals with hearing impairments and articulated a clear, well-researched solution through the Light Bell system. My approach was rooted in empathy, ensuring that every design decision was made with the end user in mind.
The research phase highlighted the gaps in existing solutions, which informed the innovative features of the Light Bell, such as customizable light alerts and smart-home compatibility. I articulated these ideas clearly in my design documentation, ensuring that the rationale behind each decision was well-explained.
Moreover, the iterative process of seeking feedback, refining the design, and testing different solutions demonstrated a commitment to creating a product that is not only functional but also thoughtfully designed. This depth of understanding is evident in the final prototype, which reflects a careful consideration of user needs, technological possibilities, and aesthetic appeal.
Light Bell is a smart doorbell system specifically designed for individuals with hearing impairments, aiming to provide a more convenient and safer home experience. By using visual signals instead of traditional sound alerts, Light Bell ensures that people with hearing difficulties are easily aware of visitors at their door.
- Key Features: When a visitor presses the doorbell, Light Bell triggers changes in the home’s lighting to alert the user. The light bulbs are connected to the system via Bluetooth or Wi-Fi and can change color or flashing patterns according to the user’s preferences, offering a personalized notification method.
- Mobile App Support: Light Bell comes with a dedicated mobile app, allowing users to customize light settings, view real-time video from the front door (if the device includes a camera), and receive instant notifications from the doorbell.
- Smart Bulb Connectivity: Users can connect the Light Bell system to their home’s smart bulbs through Bluetooth or Wi-Fi. The bulbs can not only change colors when the doorbell is pressed but can also be automated based on time of day or user needs.
- Multiple Color Options: The Light Bell prototype is designed in blue, offering visual clarity and aesthetic appeal. Different color options allow users to customize the system to match their home decor or personal preferences.
- Design and Usability: The system features a simple, user-friendly design that can be easily installed at the front door. It is both attractive and functional, making it ideal for everyday use.
Light Bell provides a straightforward yet effective solution to help individuals with hearing impairments easily manage visitor notifications. You might also consider adding a logo to the device to enhance its recognition and trustworthiness. For emergency situations, you can set specific light alerts through the app, further enhancing safety.













Recent Comments